Your organization is moving applications and assets to the cloud. How do you incorporate these apps into your security and compliance practices, adapt your IAM to fit this changing application environment, transform the business smoothly and still keep costs under control?
As your company commits strategically to cloud applications like Office 365, Salesforce, Box and dozens of other core services, how should you respond? Perhaps equally important, how should you address the broader mobile application environment?
Here’s how.

1. Assess your current IAM situation.
Based on the challenges ahead, you’ll need to define your future requirements based on gaps in your current environment. You can’t determine the real costs and benefits without a clear inventory of your current identity and authentication infrastructure and policies, including:
- What application resources are currently within your purview and what users and groups need to authenticate with which resources?
- What applications have been implemented outside IT’s control, i.e., placed into service through “Shadow IT”?
- What is your process for managing employee entitlements and provisioning new user access to business applications?
- What are your support and administration costs related to managing user identity and access?
2. Evaluate what IAM approach is right for you.
Your research will be crucial in devising a strategy and implementation plan. With this information you have most of what you need to begin evaluating requirements against capabilities and the total cost of upgrading your existing products or adopting new cloud IAM services.
Cloud solutions may well have advantages, particularly in an organization that is dispersed geographically and heterogeneous in terms of its IT resources. Other benefits include the savings that comes from greatly eased administration and maintenance associated with software-as-a-service, as compared to on-premises products.
There will also be infrastructure cost savings from going to the cloud; complicated on-premises solutions often require expensive load-balancing equipment, dedicated database servers and the expertise to run them. With a cloud solution, the service provider runs and manages all that.
Other factors to consider:
- Directory Integration
Your enterprise almost certainly relies heavily on Active Directory, and that will not be going away anytime soon. You may even have an on-premises IAM solution. Administration of your users’ access to cloud solutions through these is possible but potentially very difficult.
So your IAM solution needs to have strong integration with Active Directory. It needs to operate smoothly with AD and provide tools to import user and group information as smoothly as possible.
- Vendor Practices
Identity management is a critical part of your IT infrastructure, and plays an even more important role as these services move to the cloud. The idea of outsourcing this foundational element of your application strategy requires some diligence in understanding your cloud provider’s commitment to protecting your data and embracing practices to mitigate those risks associated with an outsourced service.
Establishing trust with your vendor selection is critical. For example, find out if vendors you’re considering are audited by third parties as part of a SOC 1, SOC 2, or other compliance framework, 2) adhere to globally recognized standards such as ISO 27001 or 3) take steps to safeguard personal information by participating in Safe Harbor or TRUSTe programs.
- Open Standards
Do your cloud application providers support standards like SAML? Are these standards supported by your IAM provider’s connectors? You should expect both your IAM and cloud application provider to support relevant standards such as SAML and SCIM and that a lack of such support will work against the vendors during evaluation. While custom connectors may be required, these configurations can be problematic and more likely to cause problems over time.
- Cost Factors
Subscription-based pricing associated with SaaS models like Cloud IAM differ from traditional perpetual licensing and maintenance models. Many organizations view subscription models as an advantage because it moves the cost from capital to the operations budgets, and includes the ongoing maintenance of the system.
It’s reasonable to assume that many support and IT costs will decrease after the adoption of an IAM solution. With a federated view across your cloud app environment, an IAM solution creates many ancillary savings. One good example is that organizations often realize they’ve over provisioned the software and services needed because the IAM can report on how many users are actively running specific applications at any one time.
3. Define a strategy for implementing your IAM plan.
The key to a successful implementation includes engaging the right stakeholders early, driving toward achievable milestones supporting early successes, and then expanding the reach and scope of your solution. Stakeholders might include representatives from your IAM, Network, Compliance and Human Resource teams.
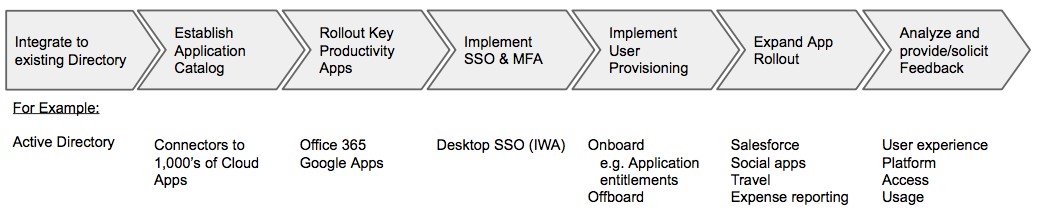
All IT projects are better off for having cooperation and buy-in from other parts of the company, especially IAM, which affects nearly everyone. Approach it step-by-step, carefully ensuring that things are working correctly, and others will see the value to them.
Consider these strategies for charting the path of your rollout:
- Directory integration
You must plan on the pre-requisite exercise of mapping your legacy directory groups and attributes into your new cloud directory and defining new roles and application entitlements. Engage your stakeholders in resolving what data is important. For example do you plan to include employee’s mobile number field in order to take advantage of any SMS forgotten password features?
- SSO (single sign-on)
The greatest and most obvious benefit to users and to IT of a good IAM implementation is enterprise single sign-on. Implement this feature to gain immediate productivity gains. Make sure users understand the SSO experience and the benefits it provides. This can be achieved through an internal communication plan that highlights the benefits of this new deployment to employees.
You may also want to consider taking the above steps with just one part of the organization initially, perhaps a single Active Directory Organizational Unit, before moving on. You can pay extra attention to that test project and move other groups over when you have the system running smoothly.
- MFA (multi-factor authentication)
As SSO gains acceptance and the federation of cloud apps begins, the need to better secure the authentication process emerges. IAM greatly eases the work involved in implementing multi-factor authentication, yet it increases demands on the end user to implement additional authentication factors. You may need to implement some of this at the same time you implement enterprise SSO, but a good second step would be to expand the use of multi-factor authentication after the SSO capabilities are rolled out successfully.
- Provisioning
Streamlining employee onboarding represents a growing focus within enterprises. Provisioning applications from the IAM system is the most common means to achieve this, however consider the need to support HR-driven workflow integrations as part of the company processes for introducing new hires to company resources. Other departments, such as Human Resources, should probably be involved in this step. You may be able to integrate user provisioning/deprovisioning from their systems through the IAM system for onboarding/offboarding.
Extending your IAM practices to support the growing cloud application environment within your organization does not need to be a large rip-and-replace exercise. The old adage evolution over revolution can be applied. This simple framework will serve you in advancing your cloud identity services in a thoughtful manner.
Chip Epps joined OneLogin as senior director product marketing in 2014 to help advance cloud security initiatives and the evolution of identity and access management. Having worked previously at Symantec, Trend Micro and Websense, he focused on securing virtual data centers and implementing SaaS-based compliance solutions. Prior to a career in security, he worked at Peregrine Systems (now HP), promoting ITSM and service management within a dynamic IT environment.
