Headlines about cybercriminals stealing user credentials are so common these days that they’re becoming old news. A few weeks ago, 13 million logins were compromised and leaked after a free website host was hacked — and that’s just one of the most-recent examples.
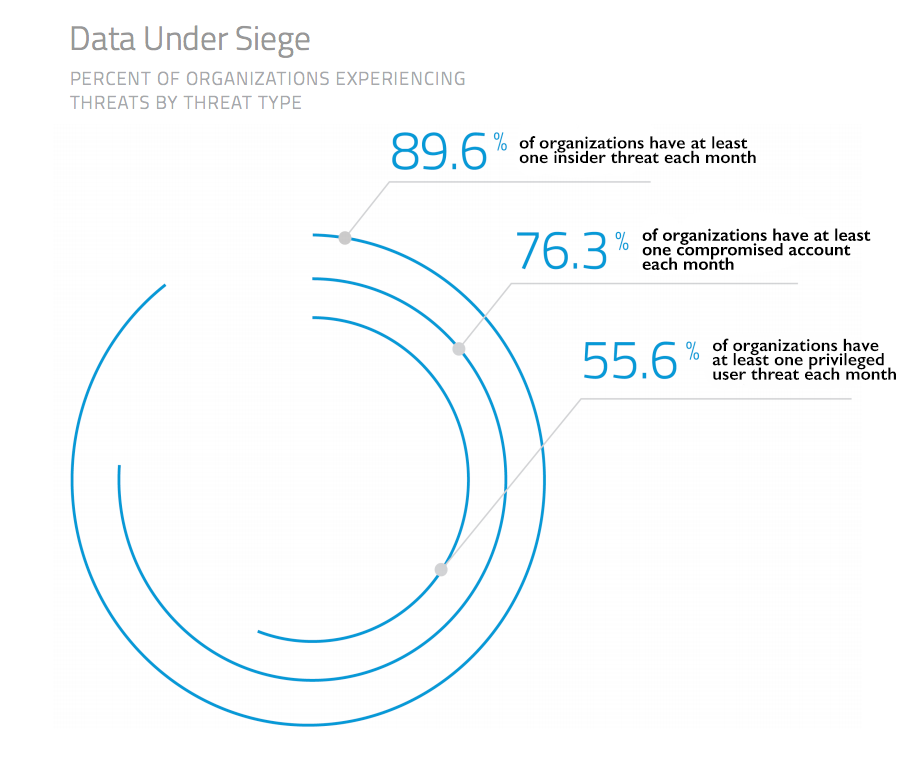
Our own data shows that slightly more than two thirds of organizations experience account compromises each month. On average, organizations experience 5.1 incidents each month in which an unauthorized third-party exploits stolen account credentials to gain access to corporate data stored in a cloud service.
Source: Skyhigh Networks, Q4 2015 Cloud Adoption & Risk Report
Our research has also uncovered that 92 percent of companies have cloud credentials for sale on the Darknet. At the average company, 12 percent of users have at least one account that has been compromised. And despite all industries being affected, it was real estate, utilities and high-tech firms that were particularly at risk.

Source: Skyhigh Networks, Q4 2015 Cloud Adoption & Risk Report
Compromised credentials are frequently sold to and used by bad actors to gain insider access into enterprises and perpetrate breaches — the massive breaches of the Office of Financial Management and Anthem are two prime examples.
But one doesn’t need to work for a high-profile organization to be at risk for breached passwords. Why? On the black market, stolen credentials can be worth more than credit card data. And the demand is high, too; since many people reuse their passwords, cracked credentials from one website or service can give bad actors access to many others.
Given the vulnerability of passwords as well as their value to cybercriminals, it’s surprising how few consumers and businesses are taking simple steps — like enabling multi-factor authentication — to protect themselves.
Why passwords are no longer enough
The sheer number of stolen online credentials is mind-boggling. One Russian crime ring alone is said to possess more than 1.2 billion login records. But the numbers make sense, considering how many major databases have been breached in the last few years.
Nearly 50 million Evernote accounts (including encrypted passwords) were compromised a couple of years ago. Within months, at least 38 million Adobe users were impacted; then eBay was hacked after employee credentials were stolen.
Earlier this year, Slack — a popular team-collaboration platform used by as many as 60 percent of organizations — had its customer information stolen, including user names and encrypted passwords. The list of these breaches goes on and on.
Hashing
One typical method that cloud-based service providers use to keep passwords safe is hashing. Similar to encryption, hashing takes plain-text passwords and turns them into a string of seemingly random numbers and letters by using a mathematical algorithm.
But hashing is not bulletproof. After LinkedIn was breached, a file with 6.5 million hashed passwords reportedly surfaced in an online Russian forum, with more than 200,000 of those passwords already cracked at the time.
Even security-minded companies like LastPass, a password manager, can make fatal errors in their hashing methods. Although following the breach earlier this year, LastPass told its customers their password vaults were not compromised; it recommended they enable multi-factor authentication going forward.
Oftentimes, cybercriminals don’t even have to worry about stealing passwords or decrypting them. More than 10 percent of users have highly unsecure passwords that contain dictionary words or simple number strings.
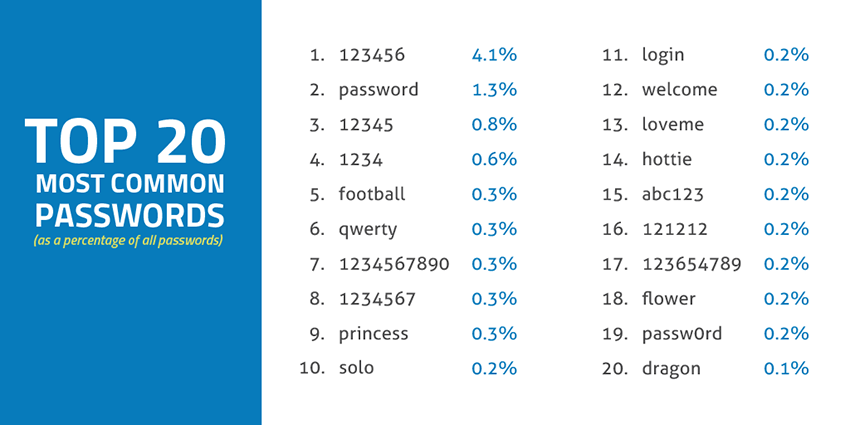
In fact, “123456” is the most popular cloud-service password, followed by “password” and “12345.” Other gems on the list of top 20 include “login,” “abc123” and “passw0rd.” By trying the most-common passwords on that list, the hackers’ success rate of gaining access grows by 10 percent.
Source: Skyhigh Networks blog, “You Won’t Believe The 20 Most Popular Passwords”
Multi-factor authentication adds a strong layer of protection
Despite the lingering security concerns surrounding cloud computing, reality is that the most popular cloud applications used at today’s enterprises are more secure than what most companies can manage with on-premises software. It’s often the risky user behavior that makes the cloud less secure.
Creating strong passwords is the first step everyone should take in protecting their online accounts. Unfortunately, the requirements for creating strong passwords are becoming increasingly complex — while the hackers’ ability to employ major computing power to crack them is becoming better and better.
This is why more and more cloud services (including LastPass, Slack and LinkedIn) are using multi-factor authentication. In today’s IT-driven world, this should be a must-have feature that both consumers and businesses employ.
Good security means multi-layered defenses. Multi-factor authentication is an essential part of “defense in depth,” mitigating password weakness. And it’s no longer feasible only for large enterprises.
The simplest and most typical form of multi-factor authentication is actually a two-step process (also called two-factor authentication or two-step verification). It works by sending a temporary code to the person’s smartphone, and the code must be used to log in along with the password. Most frequently, that’s done via a text message, but there are also apps for it, such as Google Authenticator.
This method makes access much more difficult for hackers, because they aren’t likely to have the user’s smartphone in their possession. It makes sense, too, given the proliferation of smartphones as well as the likelihood of consumers always having their phones with them.
A 2014 study found that the average person looks at his or her device 1,500 times a week, while another study found that 71 percent of respondents slept with or next to their smartphones. (And let’s face it: these days, people are more likely to return home for a forgotten phone than a wallet.)
So, with the exception of the small likelihood of a stolen, lost or malware-infected device, the smartphone is an accurate way to verify identity.
Our latest data shows that just 15.4 percent of cloud services today support multi-factor authentication. And for the ones that do support it, not all require it. At one point this summer, Dropbox was reportedly considering offering users free storage as an incentive to encourage them to use multi-factor authentication and strong account passwords.
The good news is that more and more cloud services are embracing multi-factor authentication. However, for the most part, it’s not a default setting. That means many users, including the savvier ones, won’t bother with it. Or they may simply not even know it’s available if the cloud provider added the option long after the person created an account.
Isn’t it time you turn on multifactor authentication?
Since most services don’t have a multi-factor authentication feature turned on by default, below is a list (compiled by Skyhigh Networks) of top cloud apps with links to their webpage that has directions on how to turn on multi-factor authentication.
Top 10 Consumer Services
Top 10 Enterprise Services
Sekhar Sarukkai is a co-founder and the chief scientist at Skyhigh Networks, driving the future of innovation and technology. He has more than 20 years of experience in enterprise networking, security and cloud services development.
