In 2017, we’ll see the rise of malware platforms, accelerating malware innovation and a year of shifting enterprise defense strategies. The venture capital firm Andreessen Horowitz successfully built its business under the mantra “software is eating the world.” It was reasoned that with new processes and tools in software development, coupled with infrastructure as a service, the development of software hit an inflection curve and is now 10X faster and more efficient than just 15 years ago. At Lastline, we have been measuring this same phenomenon of efficiency gains in the malware development “market.”
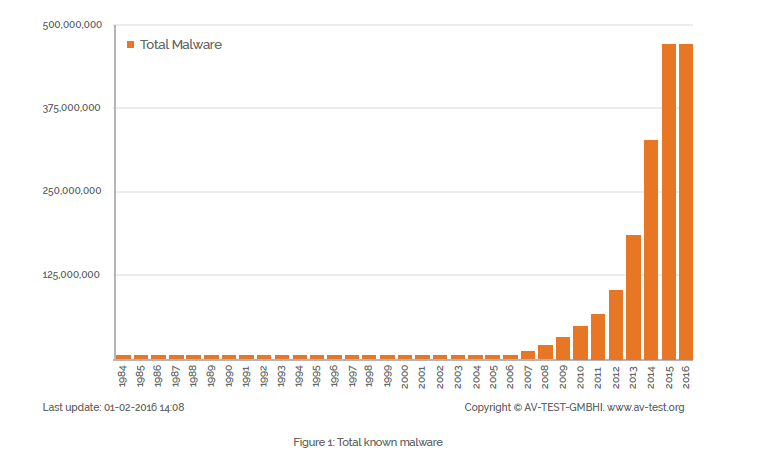
We have seen the beginnings of an expansion beyond individual, single-edition malware; and we expect that in 2017, enterprises and the data security industry will see the emergence of actual malware platform architectures. These new platforms feature pluggable and sharable services that allow for the spawn of variants faster than ever and permit code sharing between malware groups – a malevolent new type of crowdsourcing that brings the same dynamics to malware development as we’ve seen over the last decade of ethical open source software development across the commercial markets.
Since traditional means of malware detection takes a digital signature of a known malware and then combs for that specific type, variants often will change the signature profile, and attacks continue to succeed after the initial prototype malware has been identified and thwarted.
Because platform-developed malware variants can evolve and be deployed with a rapidity unseen up to this point, we predict that 2017 will be the tipping point year when malware deployments and successful attacks can – and likely will – outstrip the pace of detection by traditional signature-based detection methods, due to the rise of malware platforms.
In 2017, such rapid malware iteration-and-attack cycles will expand to become the rule and not the exception, and this will be a game changer. The effectiveness of long-trusted solutions such as hash-based malware detection will continue to decline, and – as with other areas of the software industry – computer-driven behavioral analytics will increasingly fill the void. In the fight against malware, user and entity behavior analytics (UEBA) and more advanced methods of detection will become essential.
Take code sharing through Point-of-Sale (PoS)-directed malware as an example. PoS malware has gained some significant momentum over the years and the number of families discovered in and since 2013 is drastically increasing. To build the graph below, we looked at nine different, major PoS malware “named species,” their dates of first appearance and their collection techniques. (We downloaded the code hashes of samples for each family and analyzed them closely.)
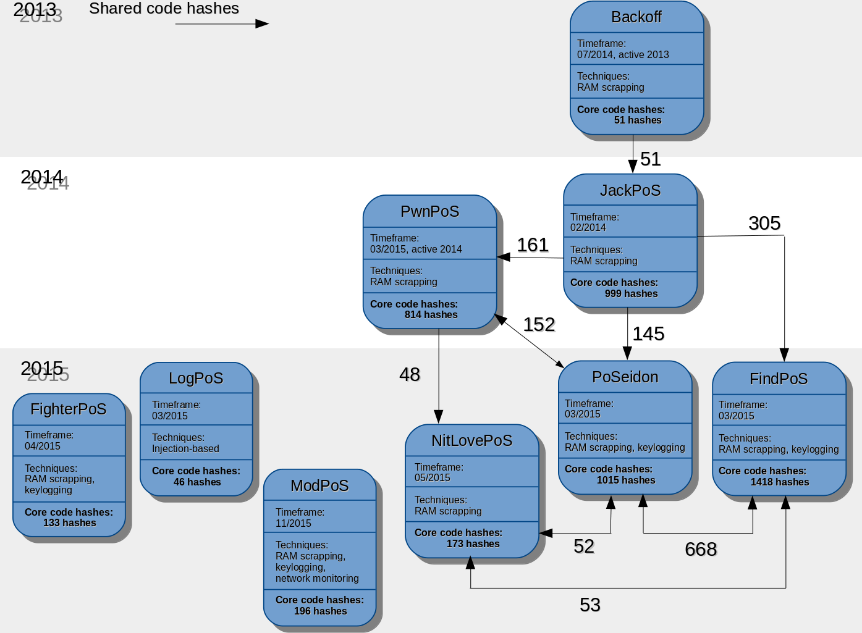
We found only three outliers: LogPoS, FighterPoS and ModPoS, whose code seems to be unique and not based on previously existing “species of origin.” On the other hand, for the six remaining named PoS malware, we found an important reuse of code portions. (In particular, one can observe a core of 45+ hashes shared across JackPoS, PwnPoS, PoSeidon, FindPoS, NitLovePoS.) All these families share the same functionality of RAM scrapping for example. The similarity is even more important between the following subset, JackPoS, PwnPoS, PoSeidon, FindPoS with 145+ code hashes in common.
Finally, if we restrict our study to the two families supporting both RAM scrapping and keylogging, PoSeidon and FindPoS, the similarity becomes prevalent with up to 65 percent of the core code of PoSeidon shared by FindPoS.
So why will 2017 become the “tipping point” when the platform-driven emergence of greater numbers of malware variants outpaces the ability of longstanding solutions to detect and thwart them? One reason is that there is finally a worldwide awareness that the problem of malware as a means to an end is huge.
Situationally we have been grappling with the prospect of state-sponsored malware having played a role in the U.S. presidential election and the realization that we’re now in a new “post-Target/Home Depot/Sony/Anthem” era where corporate hacks again hit a catastrophic peak in 2016. With malware families morphing at speeds and efficiency not seen before, security professionals will be forced to take up new tactics in the great security wars.
Look to evasive malware detection strategies that derive and act upon real-time insight that’s unique to each attack, the result of digitally observing file behaviors as a method to identify and stop threats, rather than the historic shortcut method of relying on a malware signature database of known legacy variants.
One thing we can promise is that in 2017, software will continue to “eat the world” and none of us will want to be consumed by the potentially limitless variations of malware that may tag along for the ride.
Bert Rankin is CMO of Lastline. He has over 25 years of experience successfully bringing enterprise solutions to market. Prior to joining Lastline, he served as chief marketing officer of ThreatMetrix and previously held the senior-level marketing roles at Shopcreator Services Ltd., Callidus Software, Inc. and NetManage.
